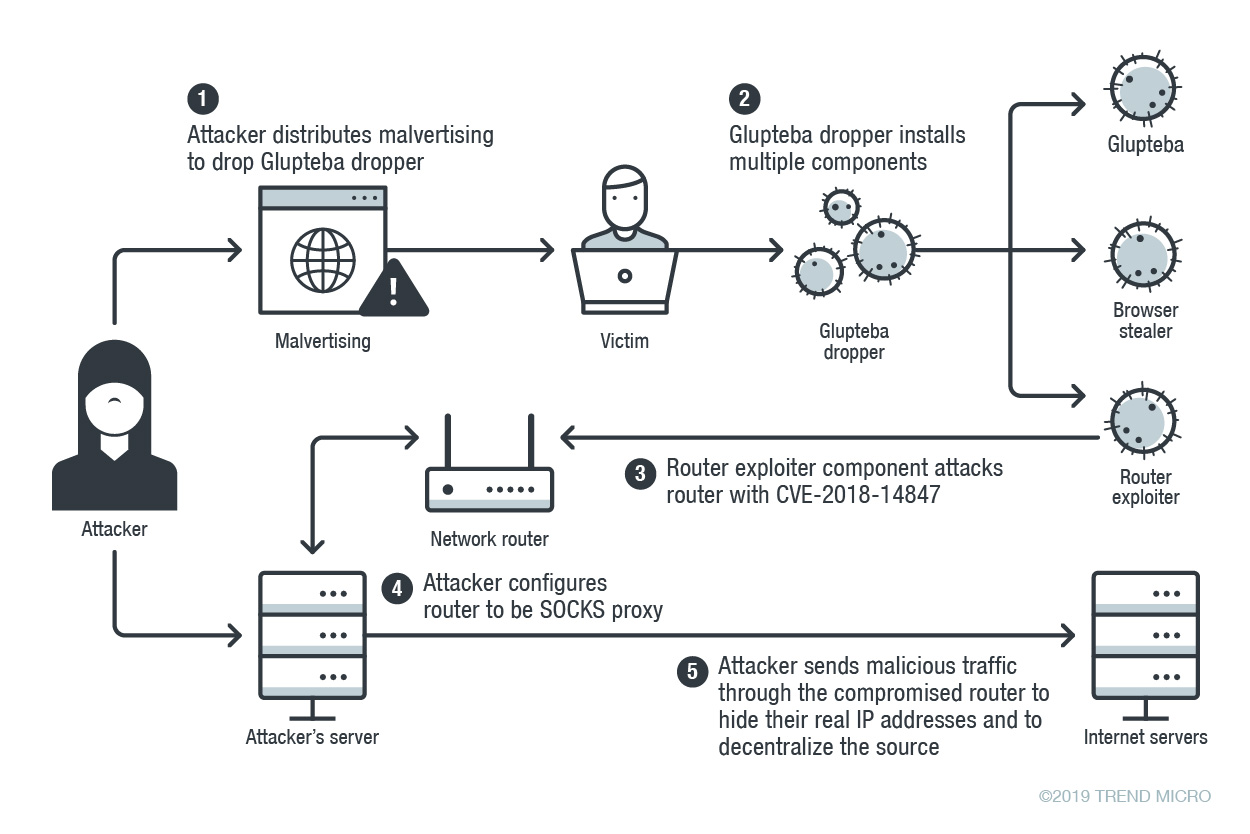
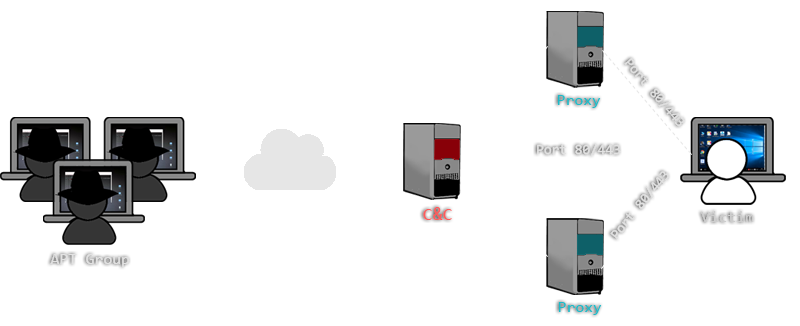
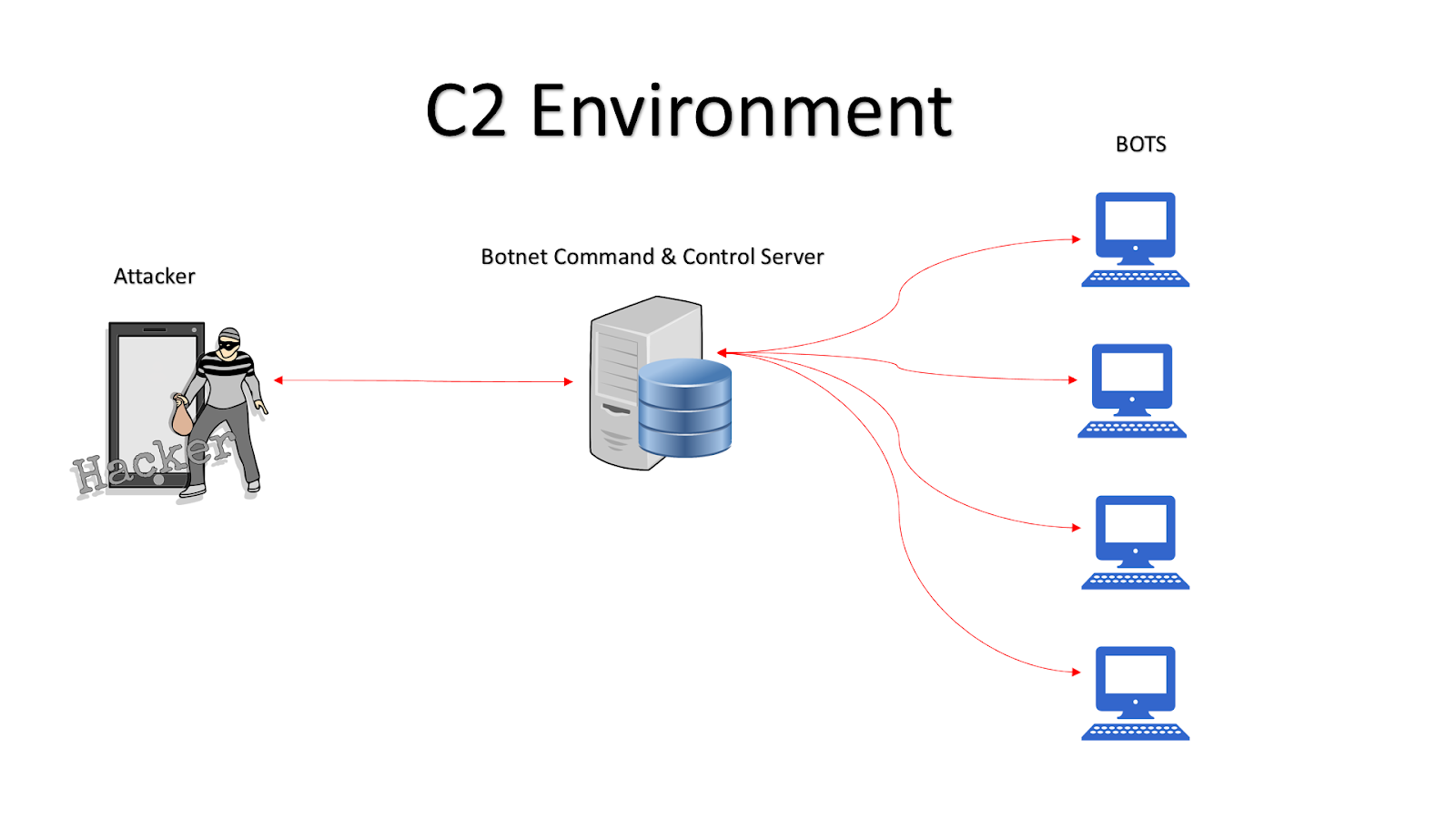
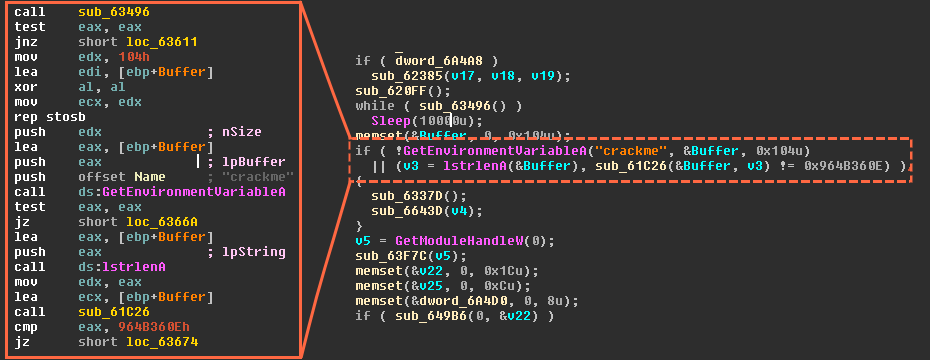
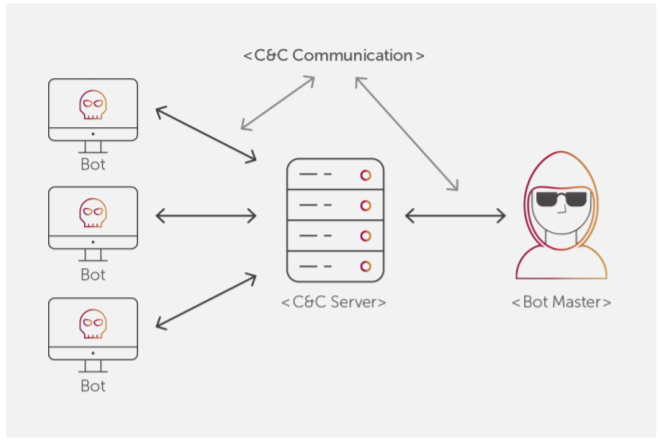
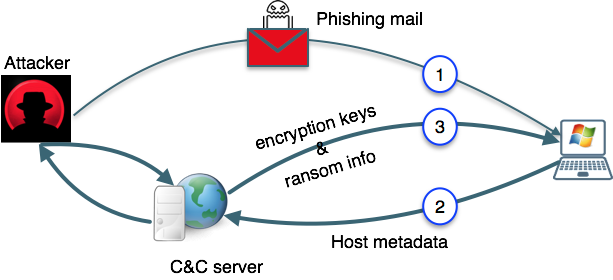
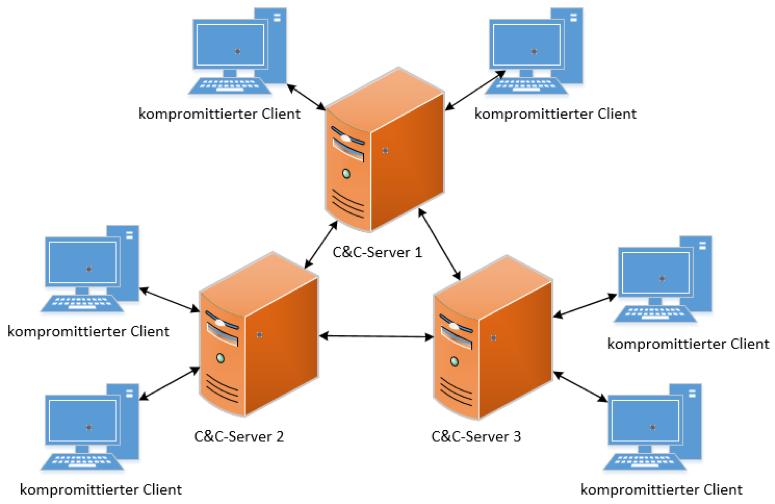
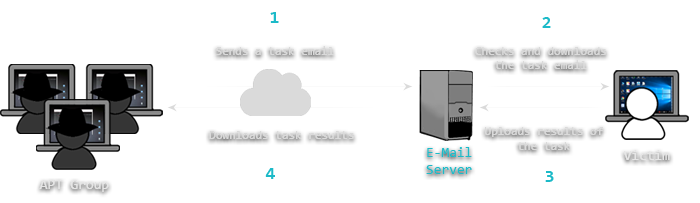
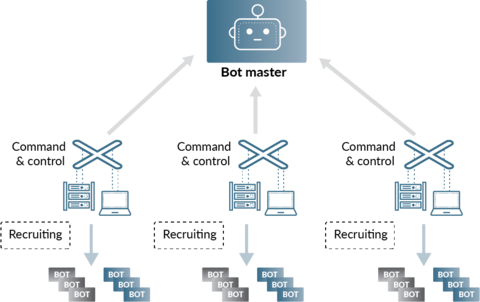
Basic entities of botnet: bots, command and control (C&C) server, and... | Download Scientific Diagram

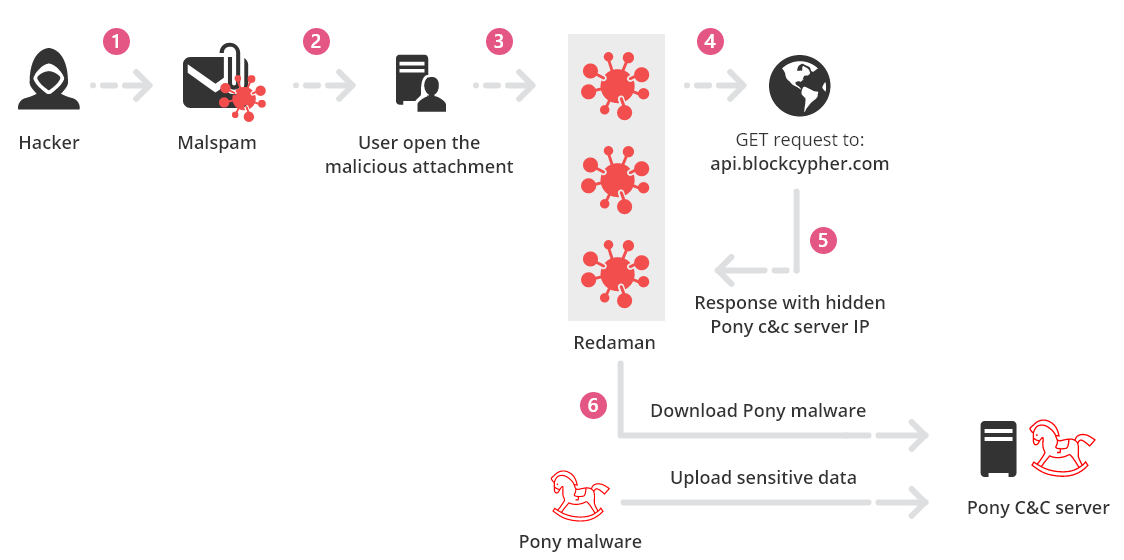
New Miori Malware Uses Text-based Protocol to Communicate with C&C Server for Launching a DDoS Attack | CyberCureME
Basic Understanding of Command and Control Malware Server - Penetration Testing and CyberSecurity Solution - SecureLayer7